Leverage Cloud Solutions for Boosted Data Safety
Leveraging cloud solutions presents an engaging service for companies seeking to fortify their data security steps. The inquiry emerges: how can the application of cloud solutions revolutionize information protection techniques and offer a durable guard versus prospective susceptabilities?
Relevance of Cloud Security
Guaranteeing robust cloud security measures is paramount in protecting sensitive data in today's digital landscape. As organizations significantly rely on cloud solutions to store and refine their information, the requirement for strong security methods can not be overemphasized. A breach in cloud safety can have extreme effects, varying from financial losses to reputational damage.
One of the key reasons that cloud safety and security is essential is the shared duty model employed by the majority of cloud provider. While the company is liable for protecting the facilities, customers are accountable for protecting their data within the cloud. This division of obligations emphasizes the value of executing durable safety steps at the user degree.
In addition, with the expansion of cyber risks targeting cloud environments, such as ransomware and information breaches, organizations must remain attentive and proactive in mitigating threats. This involves routinely upgrading protection procedures, checking for dubious activities, and enlightening workers on best techniques for cloud security. By prioritizing cloud safety, organizations can much better secure their sensitive data and maintain the count on of their stakeholders and consumers.
Data Encryption in the Cloud
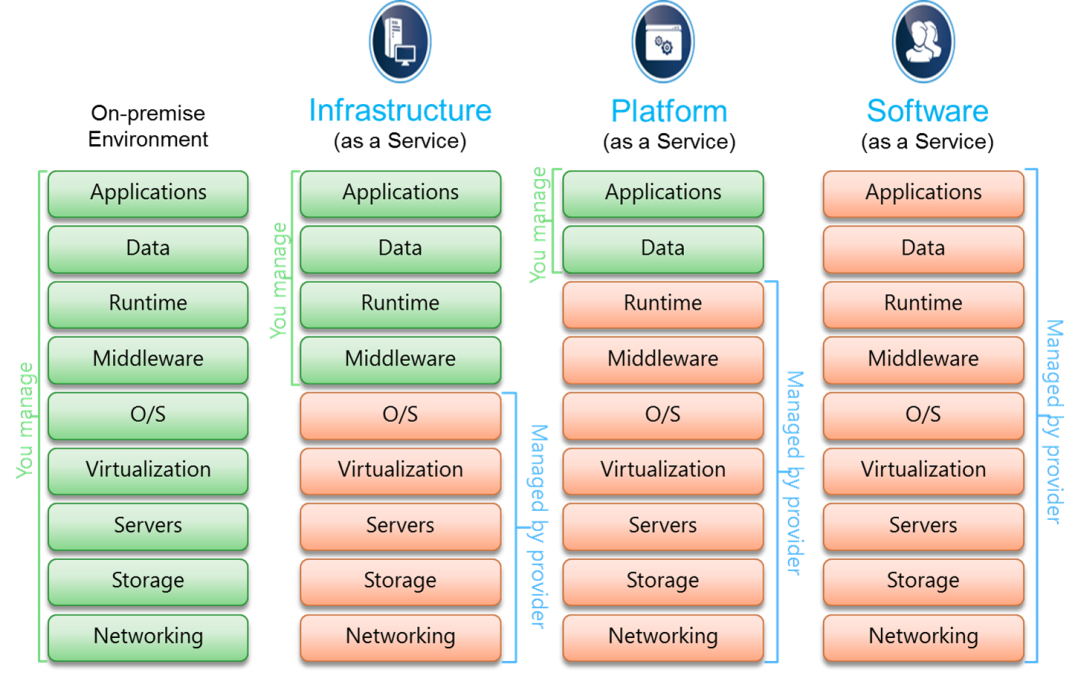
File encryption in the cloud typically entails making use of cryptographic formulas to scramble data into unreadable styles. This encrypted data can just be deciphered with the equivalent decryption secret, which includes an added layer of safety and security. Furthermore, lots of cloud provider provide file encryption mechanisms to safeguard information at rest and in transit, enhancing general data protection. Executing robust file encryption practices along with other safety and security measures can significantly boost a company's protection against cyber hazards and secure beneficial info kept in the cloud.
Secure Data Back-up Solutions
Data back-up services play an essential function in making certain the strength and safety and security of data in the occasion of unforeseen occurrences or information loss. Protected data backup options are essential elements of a robust information safety and security method. By regularly supporting information to secure cloud web servers, companies can alleviate the threats associated with data loss as a result of cyber-attacks, hardware failures, or human mistake.
Implementing safe information backup solutions involves picking dependable cloud provider that offer security, redundancy, and information honesty measures. Security guarantees that information stays protected both in transit and at rest, securing it why not try here from unauthorized accessibility. Redundancy devices such as information replication throughout geographically dispersed servers assist prevent total information loss in situation of server failures or natural catastrophes. In addition, information stability checks make sure that the backed-up information continues to be unchanged and tamper-proof.
Organizations should establish automatic backup schedules to make certain that data is consistently and successfully backed up without hands-on treatment. When needed, normal screening of information repair procedures is likewise essential to ensure the performance of the back-up remedies in recovering information. By buying protected data backup remedies, organizations can improve their data safety and security pose and decrease the influence of prospective information breaches or disturbances.
Function of Gain Access To Controls
Applying strict accessibility controls is critical for maintaining the protection and stability of sensitive details within business systems. Access controls work as a vital layer of defense versus unauthorized accessibility, making sure that just licensed individuals can watch or manipulate delicate data. By defining that can gain access to certain sources, organizations can limit the risk of data violations and unapproved disclosures.

On a regular basis reviewing and find more upgrading access controls is vital to adapt to organizational adjustments and advancing security hazards. Continual monitoring and bookkeeping of gain access to logs can help detect any kind of dubious tasks and unauthorized gain access to attempts immediately. Overall, robust access controls are basic in protecting sensitive information and mitigating security dangers within organizational systems.
Conformity and Regulations
Frequently making sure conformity with relevant laws and requirements is necessary for organizations to maintain information safety and personal privacy measures. In the realm of cloud services, where data is usually saved and processed externally, adherence to industry-specific laws such as GDPR, HIPAA, or PCI DSS is critical. linkdaddy cloud services.
Several suppliers supply file encryption capacities, access controls, and audit trails to help companies fulfill data security standards. By leveraging compliant cloud services, companies can boost their data safety position while meeting regulative responsibilities.
Conclusion
To conclude, leveraging cloud solutions for boosted data security is important for companies to secure sensitive details from unauthorized i thought about this access and possible violations. By implementing robust cloud protection protocols, including information file encryption, safe and secure backup services, gain access to controls, and conformity with laws, businesses can gain from advanced protection actions and knowledge used by cloud solution companies. This aids alleviate dangers effectively and makes certain the discretion, honesty, and availability of data.

Data back-up services play a critical role in guaranteeing the strength and protection of data in the event of unanticipated events or information loss. By consistently backing up information to secure cloud web servers, organizations can minimize the risks connected with information loss due to cyber-attacks, hardware failings, or human mistake.
Carrying out secure information backup solutions includes picking trusted cloud service suppliers that use file encryption, redundancy, and data integrity actions. By investing in safe and secure data backup services, companies can enhance their information safety stance and lessen the impact of potential data breaches or disruptions.